Overview
When your account is registered and active, you can login to your Interguard account from anywhere. From the Interguard app, download and install an agent directly on a computer or mobile device. Endpoint devices must have Internet connection to return data to Interguard.
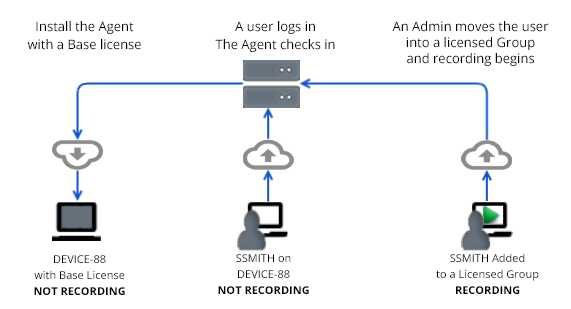
Recording begins when:
(1) The agent installation is complete and the device restarts.
(2) An end-user logs in.
(3) The installed agent reports the device and user name to the Interguard server.
(4) An Admin assigns the "Unassigned" user to a group (or assigns a Recording Policy directly to the user).
(5) The agent receives the Recording Policy from the server.
Once recording is enabled, activity is automatically and securely uploaded to the server under your account. Activity data is retained until the end of your data retention period, as established by terms of your purchase. Set up regular Exports or Reports to retain all data.
- Port 443 - The agent uses port 443 on the device for all communication.
- TLS 1.2 or higher - All website connections require a minimum of TLS 1.2 to accept communication. See Communication Requirements for a list of sites the endpoint and app need to access.
Licensing by user
For the best behavior and risk analytics, install Interguard Agent software on all devices used in your workplace. Licenses are assigned (and "used") when a user logs into the recorded device and the user is moved to a licensed Group (or assigned a Recording Policy).
The license types used are:
- Base License - Not purchased - used only to install and enable the agent to check-in and report the device name and logged-in user. No activity is recorded under this license, and it cannot be "assigned."
- Insider Risk Management - Available for purchase - Provides full event recording, screenshots, intelligent risk analysis, plus user-defined policies to manage security and compliance.
- User Activity Monitoring - Available for purchase - Provides full event recording, screenshots, analysis of productive vs. non-productive time, and a variety of alerts and reports.
What is recorded
The Recording Policy and License assigned to a user's group determines what is recorded and type of recording. Windows, Mac, Android, and Chromebook capabilities are called out below. You can view all activity in Data Explorer. For support by operating system, see the Android, Chromebook, Mac and Windows Guides.
|
Activity |
User Activity Monitoring |
Insider Risk Management* |
WIN |
MAC * |
AND * |
CHR * |
|
Login Events |
 |
 |
 |
 |
 |
|
|
Active/Idle Time |
 |
 |
 |
 |
 |
 |
| Alert on Anomalies |  |
 |
 |
 |
||
| Alert on Behaviors |  |
 |
 |
 |
 |
|
| Alert on Event Conditions |  |
 |
 |
 |
 |
|
|
Alert on Keywords |
 |
 |
 |
 |
 |
 |
|
Alert on Risk Score Change |
 |
 |
 |
 |
 |
|
|
Applications Used |
 |
 |
 |
 |
 |
 |
| Websites Visited |  |
 |
 |
 |
 |
 |
| Messaging Activity |  |
 |
 |
 |
 |
 |
| Email Activity |  |
 |
 |
 |
 |
|
| Keystrokes Typed |  |
 |
 |
 |
 |
|
| File Activity |  |
 |
 |
 |
 |
|
| File Uploads/Downloads |  |
 |
 |
 |
 |
|
| Screenshots on Accessing Programs/Websites |  |
 |
 |
 |
 |
|
| Continuous Screenshots |  |
 |
 |
 |
 |
 |
| Blocking (Websites & Apps) |  |
 |
 |
 |
||
| Activity (Productivity) Analysis and Scoring |  |
 |
 |
 |
 |
|
| Automatic Risk Analysis and Scoring |  |
 |
 |
 |
 |
*NOTES:
- Insider Risk Management - (IRM) A user license designed to work with Veriato's AI-driven predictive behavior analytics platform to provide risk detection, insights, and advanced alerting. Contact Veriato Sales to upgrade to Veriato UAM-IRM and access all features.
- User Activity Monitoring - (UAM) A user license type (formerly known as "Employee Monitoring") that provides daily productivity and workday activity tracking for onsite and remote employees. Contact Veriato Sales to upgrade to Veriato UAM-IRM and access all features.
- Productive/Unproductive activity - Applications and websites in Windows and Mac, and websites in Chromebook, can be rated for productivity.
- Mac - Browser support by OS affects activity recording. See Mac Support.
- Android - Look in Data Explorer under Mobile for Android activity. Android apps may be rated as "Risky" (a preset category) but cannot be rated as Productive or Unproductive.
- Chromebook - Website, Chat, Email, and File activities are captured within the Chrome browser.
- Screenshots on Alert Words - Will be available in the near future.
- Blocking - Available soon for Insider Risk Management.
Updated: 05/21/2024